Device Unicity in IoT Systems: A Foundational Pillar for Secure and Reliable Connectivity
Device unicity is essential for secure and reliable IoT systems, ensuring each device has a unique, immutable identity. This identity, often tied to a certificate, must be established during manufacturing and securely stored. Methods include silicon-embedded UIDs, eFuses, secure elements, and external devices like EEPROMs, 1-Wire chips, TPMs, and I²C-based secure ICs such as the ATECC608A. In modular systems, where CPU boards may be replaced, UID storage must reside in persistent components such as chassis-mounted chips or cable harnesses. Generated identifiers like GUIDs or serial numbers are also viable, provided they are securely managed and integrated with ERP systems. Device software must verify the UID and certificate before connecting to the IoT Hub, enhancing security and preventing spoofing. The article outlines best practices for implementing device unicity across various hardware configurations and emphasizes the importance of secure storage and lifecycle management.
Device Unicity in IoT Systems: A Foundational Pillar for Secure and Reliable Connectivity
In the realm of IoT, device unicity is a foundational principle that ensures each device is uniquely identifiable and securely integrated into the system. Without unicity, devices may conflict due to misconfiguration, leading to operational failures and security vulnerabilities. This article explores the importance of device unicity, its role in enhancing security, and the various methods for implementing it across embedded systems.
Importance of Device Unicity
Device unicity guarantees that each IoT device has a distinct identity, preventing duplication and ensuring traceability. This identity must be immutable and established during manufacturing. A certificate, bound to the device’s unique identifier (UID), is loaded into the device to authenticate its identity.
The UID must be based on information that cannot be altered post-production. This can reside internally (e.g., silicon-embedded identifiers, eFuses) or externally (e.g., secure elements). The certificate, issued by a trusted Certificate Authority (CA), binds the UID to a cryptographic key, enabling secure authentication and communication.
Ensuring unicity is critical for device provisioning, lifecycle management, and secure cloud connectivity. It prevents unauthorized devices from joining the network and supports compliance with security standards. Manufacturers must implement robust processes to generate, store, and protect UIDs and certificates, ensuring they remain tamper-proof and verifiable throughout the device’s life.
Enhance the Device Security by Checking Certificate
Device software plays a vital role in verifying the UID and its associated certificate before establishing a connection to the IoT Hub. This verification process includes:
- Reading the UID from the designated hardware location.
- Validating the certificate against a trusted root CA.
- Ensuring certificate integrity, including signature and expiration checks.
- Confirming UID–certificate binding to prevent spoofing.
This process ensures that only legitimate devices can connect to the IoT platform. It also protects against man-in-the-middle attacks and unauthorized access. By integrating certificate checks into the firmware, devices can perform mutual authentication with the IoT Hub, enhancing trust and security.
In high-security environments, this verification can be extended to include hardware-backed attestation, where the device proves its identity using secure cryptographic operations. This approach is particularly valuable in industrial, healthcare, and critical infrastructure applications, where device integrity is paramount.
Device Unicity Information Location
The location of the UID within the device must be secure and immutable. Several options are available:
- Silicon-embedded UID: Many microcontrollers and microprocessors include a factory-programmed UID embedded in the silicon. This identifier is read-only and cannot be modified, making it ideal for secure applications.
- Electronic Fuses (eFuses): Some CPUs offer programmable fuses that can be burned during manufacturing. These fuses store a permanent UID and are resistant to tampering.
- Secure Elements: Dedicated chips designed to store cryptographic keys and UIDs securely. These are often used in payment systems and high-security IoT devices.
- External EEPROMs: These can store UIDs with write protection enabled post-programming to prevent modification.
Each method offers different levels of security, cost, and flexibility. Silicon-based solutions are cost-effective and secure but may lack customization. Secure elements provide high security but increase BOM cost. EEPROMs offer flexibility but require careful handling to prevent tampering.
The choice of UID location should align with the device’s security requirements, manufacturing capabilities, and lifecycle management strategy.
Device Unicity on an External Device
External devices, accessible via CPU buses such as I²C, SPI, or 1-Wire, offer flexible options for storing UIDs. These include:
- EEPROMs with write protection: Once programmed, these devices can be locked to prevent data alteration, ensuring UID integrity.
- 1-Wire devices like DS2401: These chips come with a factory-programmed, globally unique 64-bit identifier. They are simple to integrate and cost-effective.
- I²C devices like Maxim ATECC608A: These secure elements embed a GUID and provide secure storage for device certificates, supporting cryptographic operations and secure authentication.
- TPMs (Trusted Platform Modules): These provide secure storage for UIDs and cryptographic keys, supporting advanced security features like attestation and encryption.
- Other PCB-mounted chips: Secure microcontrollers or authentication ICs can also serve as UID storage devices.
Using external devices allows for modular design and easier integration of secure identity features. However, it introduces complexity in hardware design and software communication. Designers must ensure secure access to these devices and protect against spoofing or replacement.
Communication protocols should include authentication and encryption to safeguard UID data. Firmware must be designed to detect and respond to anomalies, such as UID mismatches or certificate failures.
Device Unicity on an External Device That Does Not Reside on the CPU Board
In modular IoT systems, the CPU board may be replaced during maintenance. To preserve device unicity, the UID must reside on a component that remains with the device throughout its lifecycle. Options include:
- Chassis-mounted secure elements: These remain with the device even if the CPU board is swapped, ensuring continuity of identity.
- Cable harnesses with embedded UID chips: These can include 1-Wire devices or EEPROMs with locked UIDs, integrated into the wiring.
- Peripheral boards: Non-replaceable boards within the device can host the UID and certificate.
This approach ensures that the device retains its identity regardless of CPU board changes. It simplifies maintenance and avoids the need to re-register devices with the IoT platform.
Designers must ensure that the UID storage component is tamper-resistant and securely connected to the CPU. Communication between the CPU and the UID device should be authenticated and encrypted to prevent spoofing.
This strategy is particularly useful in professional equipment, such as connected coffee machines or industrial controllers, where field maintenance is common and device identity must remain consistent.
Generated Device Unicity Information
In some cases, the UID is generated during manufacturing rather than derived from hardware. Common formats include:
- GUIDs (Globally Unique Identifiers): 128-bit values that are statistically unique and suitable for software-based identity.
- Serial numbers: Assigned by the manufacturer and tracked in the ERP system.
These identifiers must be carefully managed to avoid duplication. They should be securely stored in the device and associated with a certificate to ensure authenticity.
Integration with the company’s ERP system ensures traceability and supports after-sales services, warranty claims, and device recalls. The UID should be linked to product metadata, manufacturing records, and service history.
Generated UIDs offer flexibility and scalability but require robust backend systems for issuance, tracking, and revocation. Security measures must be in place to prevent unauthorized generation or reuse of identifiers.
Conclusion
Device unicity is a critical pillar of secure and reliable IoT systems. Whether embedded in silicon, stored in external chips, or generated during manufacturing, the UID must be immutable, verifiable, and securely stored. Coupling the UID with a certificate enhances security and enables trusted communication with cloud services.
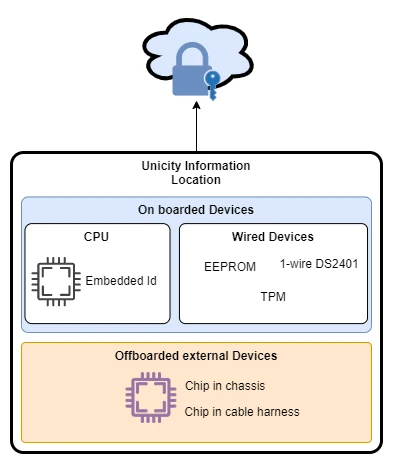
Designers must choose the appropriate method and location for UID storage based on the device architecture, security requirements, and maintenance strategy. In modular systems, offboarding the UID to a persistent component ensures continuity and simplifies field operations.
For organizations seeking guidance on implementing robust device unicity strategies, Nestedbytes offers expert consulting and tailored solutions to meet your IoT architecture needs.



