Device Unicity: How to Handle Devices within DPS and Manufacturing?
In large-scale IoT deployments, ensuring device unicity—the guarantee that each device has a unique and verifiable identity—is essential for secure communication, traceability, and lifecycle management. When provisioning devices at manufacturing time, this principle becomes even more critical. Azure IoT Hub Device Provisioning Service (DPS) is designed to automate and secure the onboarding of millions of devices, ensuring each one is uniquely identified and provisioned to the correct IoT Hub instance. This article explains how to handle device unicity using DPS, what risks arise if it's not enforced, and how to implement secure provisioning during manufacturing.
Understanding Device Unicity in DPS
What Is Azure DPS?
Azure Device Provisioning Service (DPS) is a helper service for Azure IoT Hub that enables zero-touch, just-in-time provisioning of devices to the appropriate IoT Hub without requiring manual configuration[1].
DPS supports multiple attestation mechanisms:
- X.509 certificates
- Trusted Platform Module (TPM)
- Symmetric keys
Each device is uniquely identified using one of these mechanisms, ensuring device unicity from the moment it connects.
What Happens If Device Unicity Is Not Enforced?
- Security Breaches : If multiple devices share the same identity, a compromised device could impersonate others, making it impossible to isolate threats.
- Data Attribution Errors : Telemetry from different devices may be misattributed, leading to incorrect analytics and operational decisions.
- Provisioning Failures : Without unique identities, DPS cannot correctly assign devices to IoT Hubs, leading to provisioning errors or conflicts.
- Compliance and Auditing Issues : Security standards require traceability and accountability, which are only possible with unique device identities.
How to Handle Device Unicity with DPS
Step 1: Choose an Attestation Mechanism
- X.509 Certificates: Ideal for high-security environments. Each device has a unique certificate signed by a trusted CA.
- TPM: Hardware-based identity, often embedded during manufacturing.
- Symmetric Keys: Easier to implement but less secure; suitable for constrained environments.
Step 2: Register Devices in DPS
Each device must be registered with a unique identity:
- For X.509, register the certificate thumbprint or use a verified CA.
- For TPM, register the endorsement key.
- For symmetric keys, register a unique key per device.
Step 3: Link DPS to IoT Hub
DPS must be linked to one or more IoT Hubs. Devices are assigned based on allocation policies (e.g., lowest latency, geo-location, or custom logic).
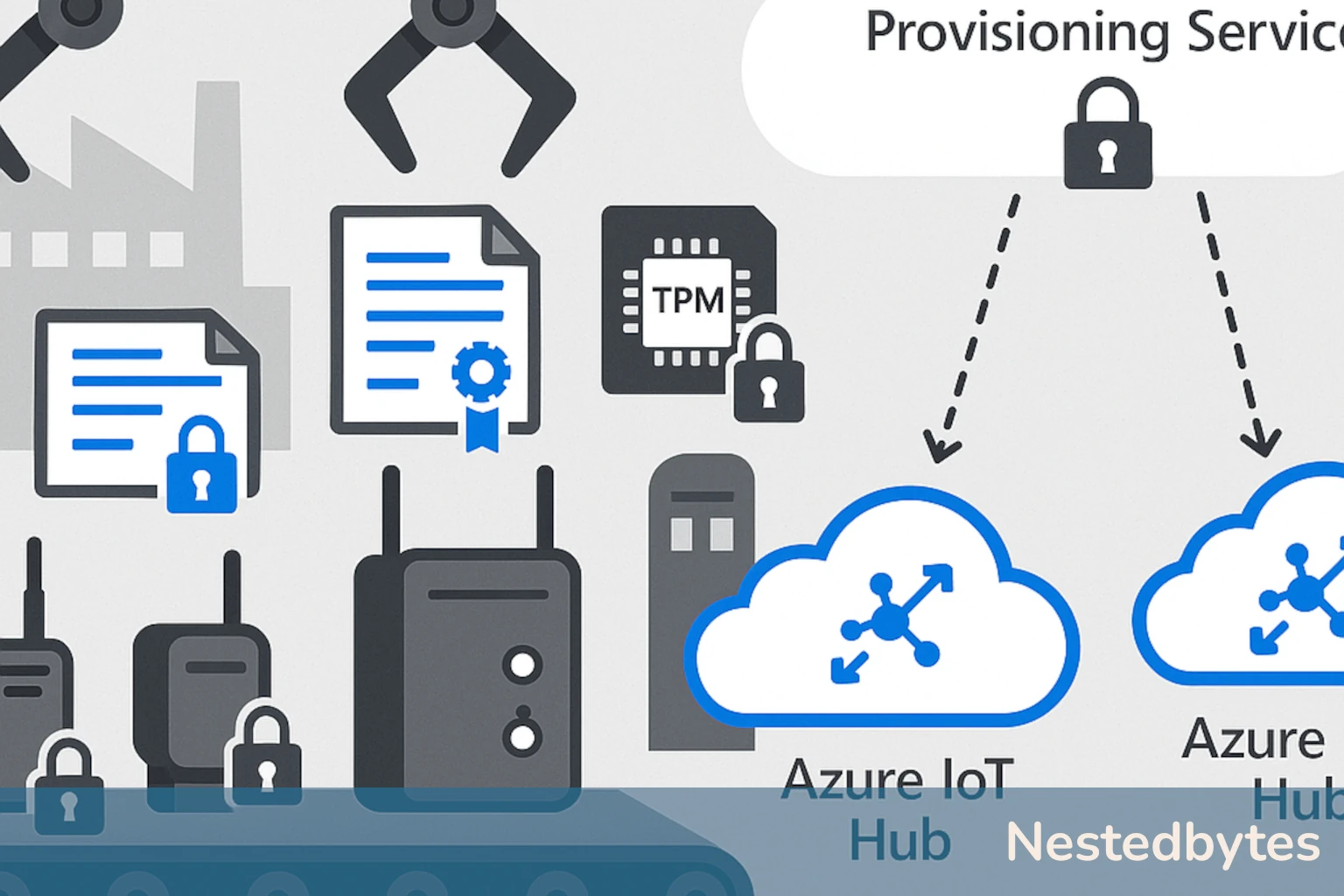
How to Provision Devices During Manufacturing
1. Embed Identity at Factory
- Embed a TPM chip or X.509 certificate during manufacturing.
- Ensure each identity is unique and securely stored.
2. Automate Enrollment
- Use bulk enrollment in DPS to register devices before shipment.
- For X.509, use a verified CA to streamline enrollment.
3. Enable Zero-Touch Provisioning
- Devices connect to DPS on first boot.
- DPS authenticates the device and assigns it to the correct IoT Hub.
- The device receives its IoT Hub connection string and begins operation.
Conclusion
Device unicity is a foundational requirement for secure and scalable IoT deployments. Azure DPS provides a robust framework to enforce this principle, especially during manufacturing, where embedding unique identities ensures secure, zero-touch provisioning.
By leveraging DPS with X.509 or TPM-based attestation, manufacturers and solution integrators can streamline onboarding, reduce operational costs, and enhance security from day one.