Device Unicity: Handle Device Unicity with X.509 Certificates
In the Internet of Things (IoT), device unicity—ensuring each device has a unique, verifiable identity—is essential for secure, scalable, and manageable deployments. As IoT ecosystems grow, the need for robust identity mechanisms becomes critical. One of the most secure and scalable methods to enforce device unicity is through X.509 certificates. This article explores how X.509 certificates help enforce device unicity in Azure IoT Hub, what risks arise when unicity is not maintained, and why adopting this approach is a best practice for modern IoT solutions.
Device unicity means that each device in your IoT solution has a unique identity. This identity is used to authenticate the device, authorize its actions, and manage its lifecycle.
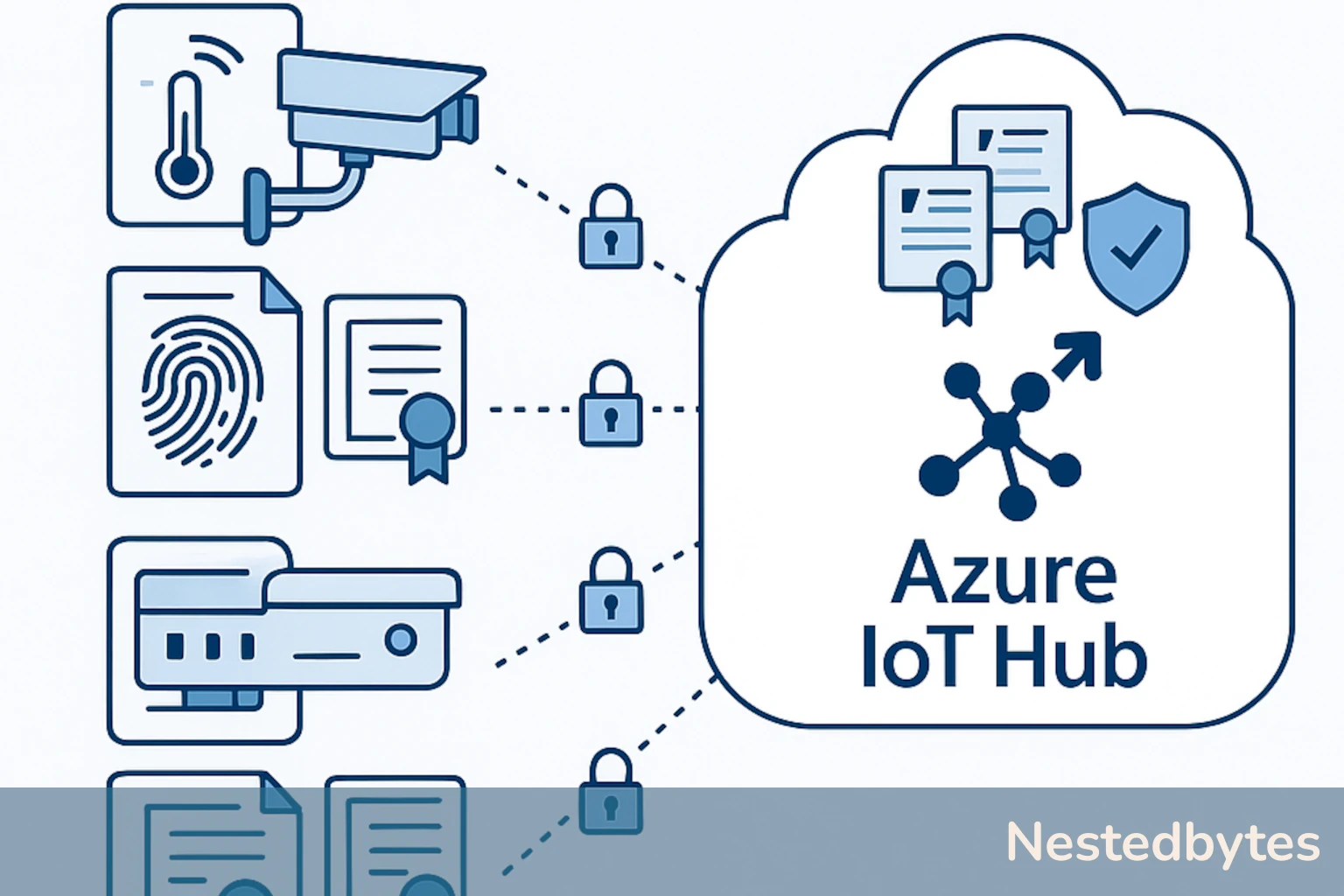
In Azure IoT Hub, device identities are stored in the Device Identity Registry, and each device must be registered with a unique deviceId. Authentication can be done using Shared Access Signatures (SAS) or X.509 certificates, with the latter offering stronger security and better scalability.
What Are X.509 Certificates?
X.509 certificates are digital certificates that conform to the IETF’s RFC 5280 standard. They are used in Azure IoT Hub to authenticate devices during TLS handshake. There are two main types:
- Self-signed certificates: Each device has its own certificate, and the thumbprint is registered in IoT Hub.
- CA-signed certificates: Devices are issued certificates signed by a trusted Certificate Authority (CA). The CA’s root or intermediate certificate is uploaded to IoT Hub, allowing multiple devices to authenticate using certificates in the same trust chain.
What Happens If Device Unicity Is Not Enforced?
- Security Risks : Without unique identities, it’s impossible to isolate and revoke access for compromised devices. Shared identities can be exploited for unauthorized access.
- Data Integrity Issues : Telemetry from multiple devices may be misattributed, leading to incorrect analytics and decisions.
- Operational Challenges : Device management tasks like firmware updates, diagnostics, and decommissioning become unreliable when devices are indistinguishable.
- Compliance Failures : Security standards such as ISO/IEC 27001 and NIST require traceability and accountability, which depend on unique device identities.
Why Use X.509 Certificates to Enforce Device Unicity?
- Strong Authentication : X.509 certificates provide cryptographic proof of identity, making them more secure than symmetric keys.
- Scalability : With CA-signed certificates, you can manage thousands or millions of devices using a single trusted root certificate.
- Simplified Provisioning : Using Azure Device Provisioning Service (DPS) with X.509 CA certificates allows for zero-touch provisioning at scale.
- Lifecycle Management : Certificates can be rotated, revoked, and audited, supporting long-term device lifecycle management.
Best Practices for Implementing X.509-Based Device Unicity
- Use CA-Signed Certificates: Prefer CA-signed over self-signed certificates for production environments.
- Register Devices with Unique Identities: Each device should have a unique certificate or thumbprint.
- Automate Provisioning with DPS: Use Azure DPS to automate secure provisioning of devices using X.509 attestation.
- Monitor and Audit: Regularly audit certificate usage and monitor for anomalies.
Conclusion
Device unicity is a cornerstone of secure and scalable IoT systems. By leveraging X.509 certificates, especially CA-signed ones, you can enforce strong, verifiable identities for every device in your fleet. This not only enhances security but also simplifies provisioning, management, and compliance.
For any organization building or scaling an IoT solution, adopting X.509-based device unicity is not just a recommendation—it’s a necessity.